 Hello!!!
Hello!!!
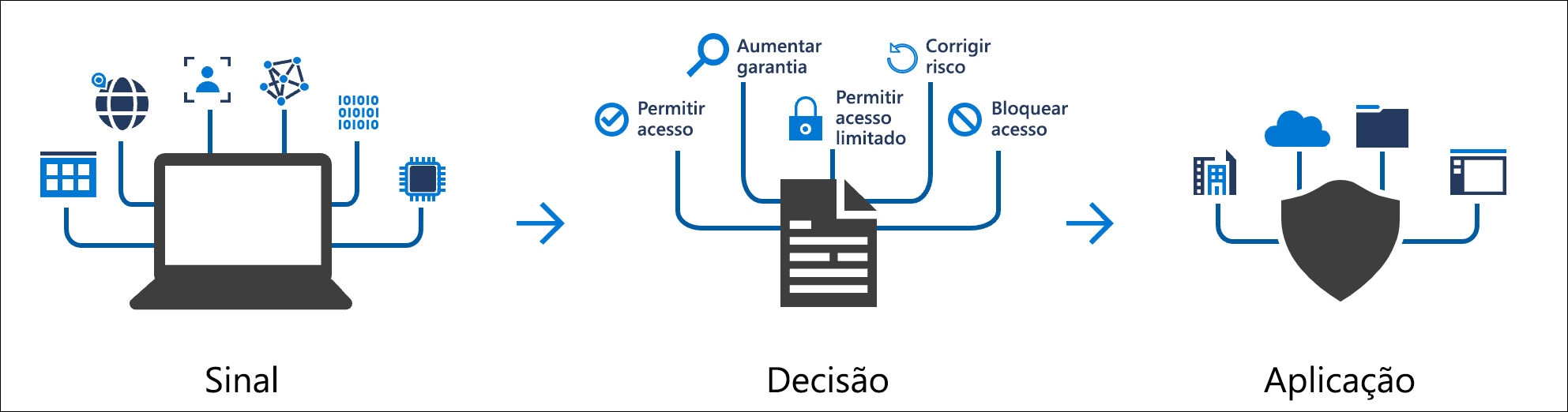
Conditional access policies are if-then instructions, if a user wants to access a resource, then they must complete an action first.
According to Microsoft, commonly applied policies are:
Require multifactor authentication for users with administrative roles Require multifactor authentication for Azure management tasks Block user entries attempting to use legacy authentication protocols Require trusted locations for Azure Multifactor Authentication registration Block or allow access in specific locations Block risky sign-in behaviors Require organization-managed devices for specific applications
Very important, to use this feature you must have at least one “premium” license from your Azure Active Directory.
As a demonstration, I will enforce MFA (Multifactor Authentication) for all administrative users.
Step by Step:
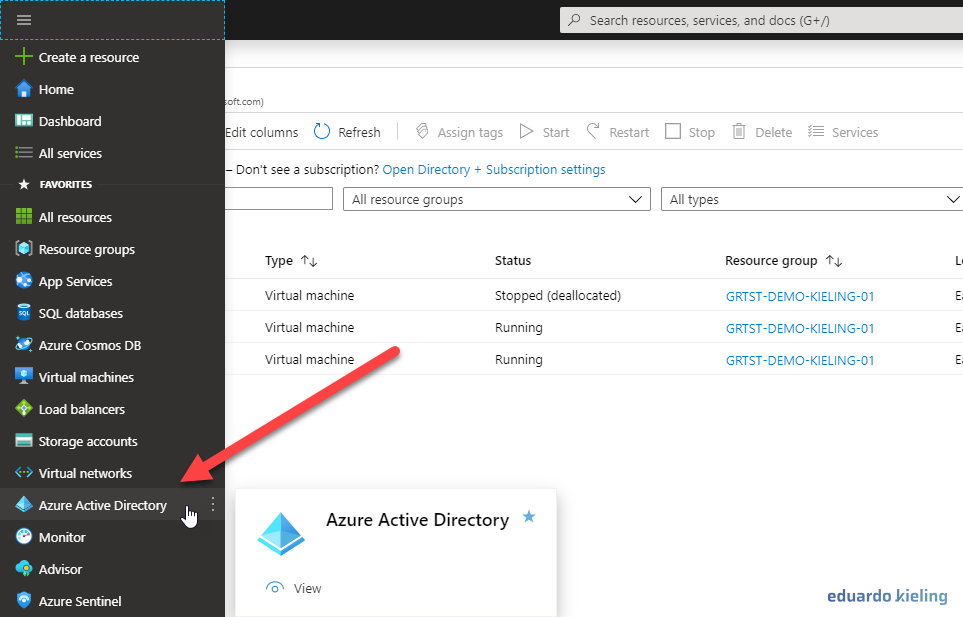
- Log in to your Azure portal and look for the “Azure Active Directory” item in the menu, as shown in the image below, and click on it:
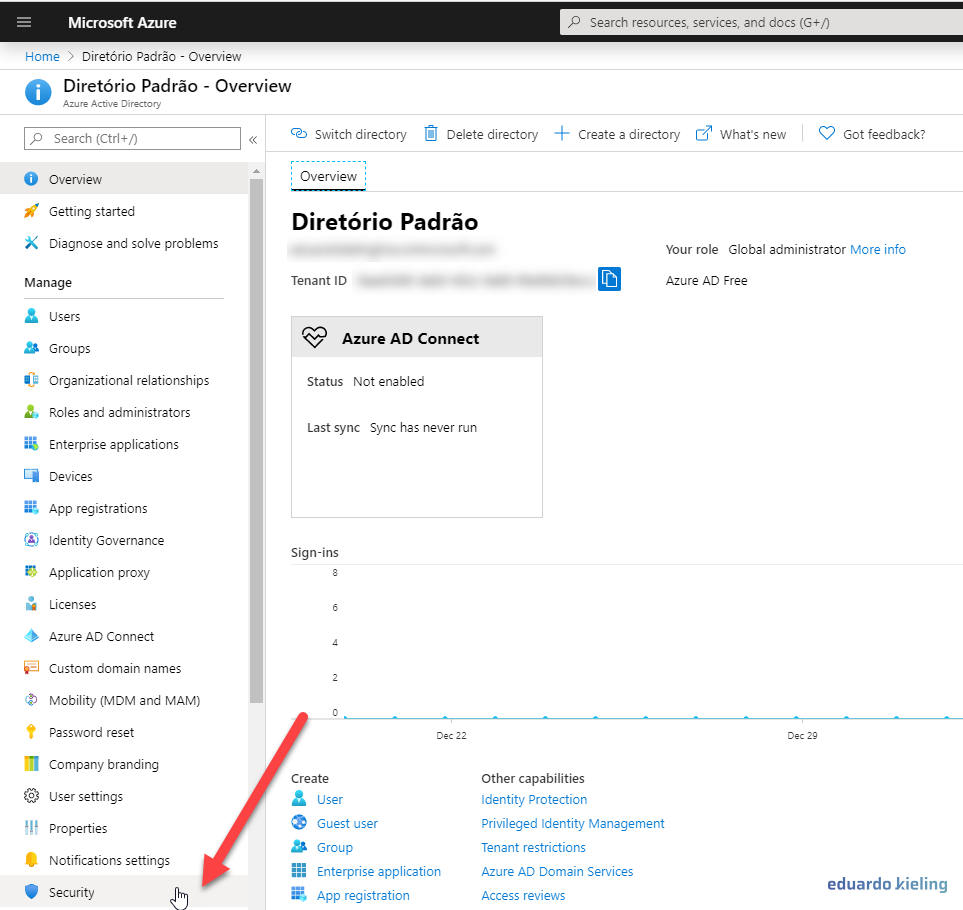
- Within Azure Active Directory, we go to “Security”
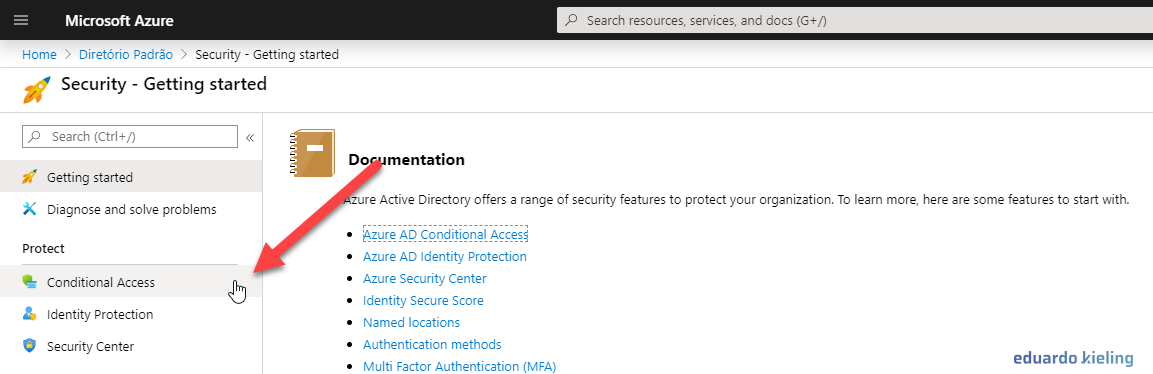
- Within the security tab, we go to the “Conditional Access” item:
- Ready, we have arrived where we wanted, this is where we can define our custom policies. As a demonstration, I will enable one of the policies. Note that they all appear with the status “OFF” (Off).

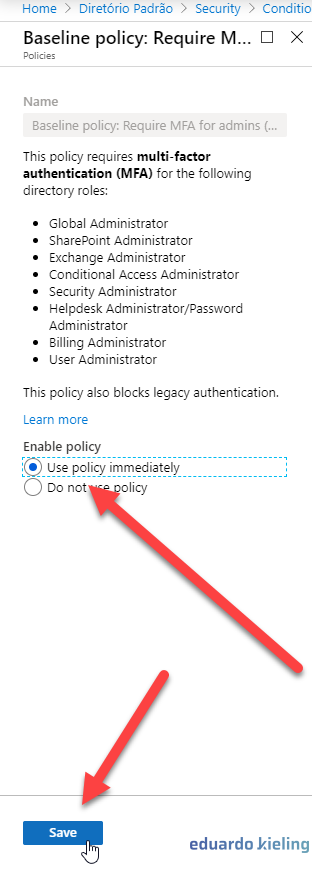
- By clicking on the policy below, we can configure it to force administrative users in your environment to use MFA (Multifactor Authentication). To activate it, check the “Use this policy immediately” option.
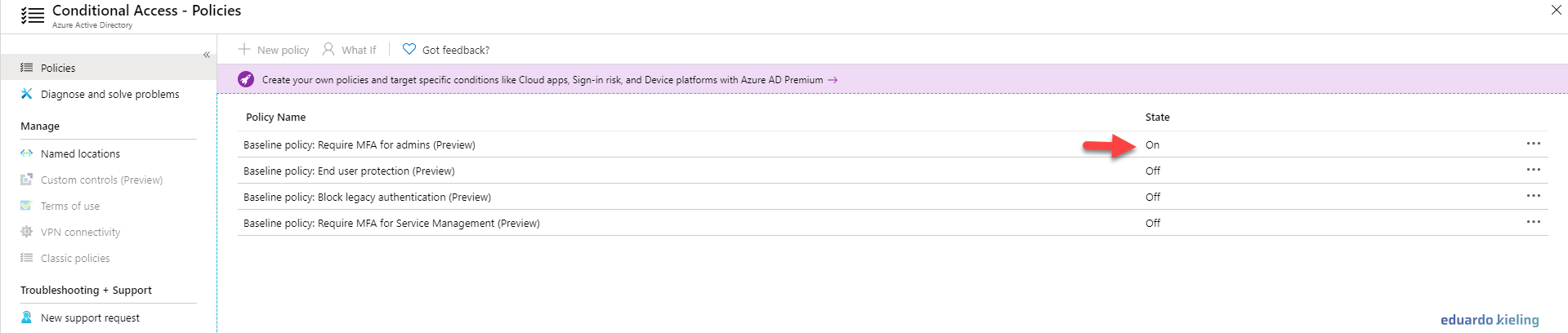
- As you can see, now our policy appears as enabled, which means that no administrative user will be able to log in to your environment without using MFA:
 and that’s it folks, I hope you enjoyed it!
and that’s it folks, I hope you enjoyed it!
Until next time
Eduardo Kieling
