Hello Guys,
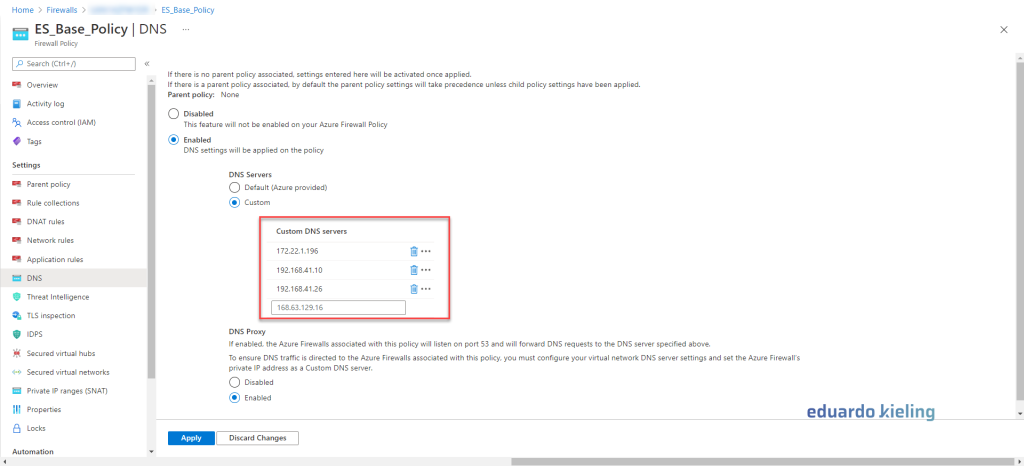
Azure Firewall is a cloud-native network security service that protects your Azure resources and applications. It operates in a transparent proxy mode by default, which means that traffic is sent to the firewall using a user defined route (UDR) configuration. The firewall intercepts that traffic inline and passes it to the destination.
However, there is another mode that you can use for your outbound traffic: Explicit proxy. This mode allows you to configure a proxy setting on the sending application, such as a web browser, with Azure Firewall acting as the designated proxy. This way, traffic from the sending application goes to the firewall’s private IP address and egresses directly from the firewall without the need for a UDR.
Continue reading “Azure Firewall’s Explicit Proxy feature (preview)”

 Hello!!!
Hello!!!